Oct 19, 2013 I'm a big fan of the Cisco Anyconnect VPN client due to its easy configuration, and the relative ease of deployment to end users. When you deploy an Anyconnect VPN on your ASA, one of the important tasks is to decide how to advertise the VPN assigned addresses into the rest of your network. Apr 28, 2020 Services like Microsoft Office 365 and remote access VPN can all benefit from having an additional layer of security. This document will illustrate how you can integrate Microsoft Azure MFA into a Cisco ASA AnyConnect implementation. In addition to MFA, this example also uses LDAPS to authorize access to network resources for different groups. ASA Verification In this lesson we will see how you can use the anyconnect client for remote access VPN. Anyconnect is the replacement for the old Cisco VPN client and supports SSL and IKEv2 IPsec. When it comes to SSL, the ASA offers two SSL VPN modes. Anyconnect is the replacement for the old Cisco VPN client and supports SSL and IKEv2 IPsec. When it comes to SSL, the ASA offers two SSL VPN modes: Clientless WebVPN. The newest generation of remote access VPNs is offered from Cisco AnyConnect SSL VPN client. This is supported by Cisco ASA 8.x. The AnyConnect SSL VPN provides the best features from both of the other VPN technologies (IPSec and Web SSL). With AnyConnect, the remote user has full network connectivity to the central site.
I’m a big fan of the Cisco Anyconnect VPN client due to its easy configuration, and the relative ease of deployment to end users. When you deploy an Anyconnect VPN on your ASA, one of the important tasks is to decide how to advertise the VPN assigned addresses into the rest of your network. Fortunately, this is easy to accomplish using route redistribution.
Basic Setup
In this example, my VPN pool will be assigned from the 192.168.254.128/25 range, and I will redistribute these routes into OSPF. Notice that the ASA automatically creates a static host route for a connected client:
So we have the building blocks for what we need, now let’s look at the configuration.
There are several different ways to accomplish this task, but I’ll demonstrate what I typically use.
Redistributing into OSPF
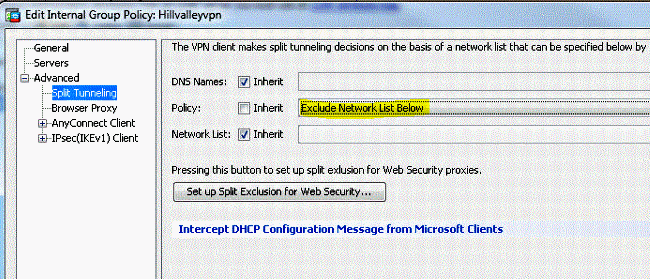
First, we’ll create a prefix list to match the address pool for our Anyconnect clients:
This prefix list entry matches the 192.168.254.128/25 subnet, as well as any routes with a mask less-than or equal to 32 bits. This works great, because our routes will all be /32.
Next we’ll create a route-map that we can reference inside OSPF:
And finally, we’ll add enable redistribution in OSPF:
If we look the routing table on another router in our network, we should see the route:
Advertising the subnet instead of individual host routes
If you like to keep your routing tables uncluttered, you might be inclined to only redistribute the entire VPN prefix, instead of the /32 routes. The important thing to remember here is that OSPF will not redistribute a route that is not already in the routing table.
We’ll simply add a static route for the VPN prefix:
Without any other modifications, we will now see routes like this in our network:
But we want to get rid of the /32 routes. So we have two options now:
- Modify the prefix-list to match only the /25 route
- Modify the OSPF redistribution command to ignore subnets.
Option 1: Modify the prefix-list
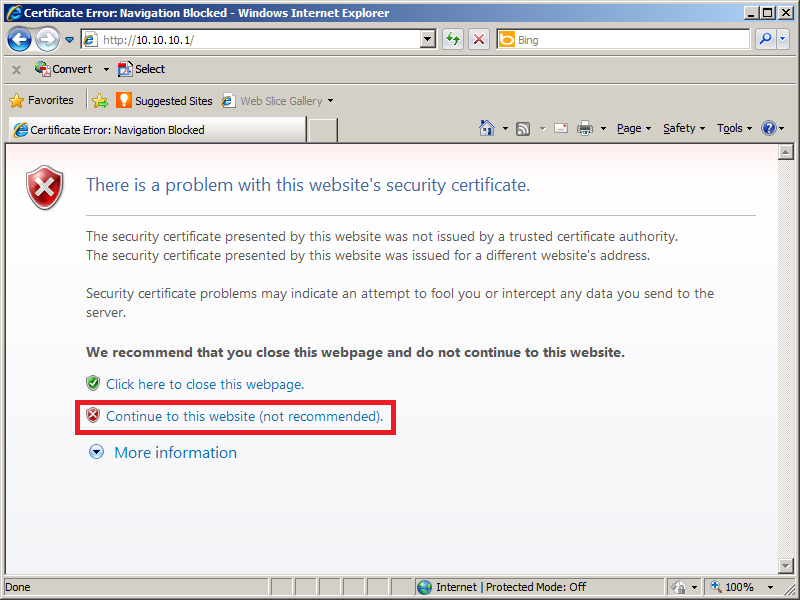
Cisco Asa Anyconnect Vpn Configuration
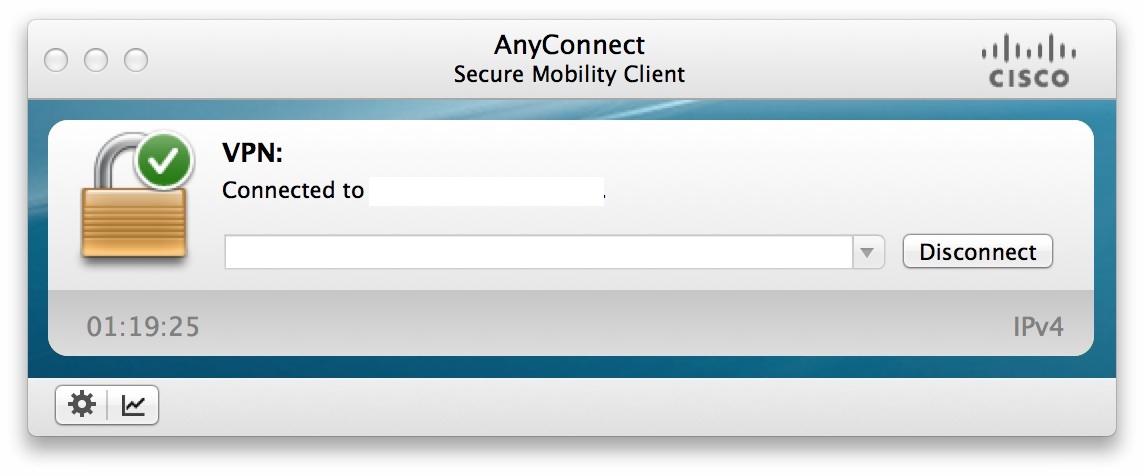
We’ll change the prefix list so we don’t even consider subnets with different masks:
Our redistribution command still has the subnets keyword, but since the prefix list won’t even allow smaller prefix lengths, we end up with just the one route.
Option 2: Modify the OSPF redistribution command
You can also remove the subnets keyword from the redistribution command:
Cisco Asa Anyconnect Vpn
This way it doesn’t matter if the prefix-list matches longer routes, OSPF just won’t redistribute them.
Final Configuration
In the end we have a configuration that looks something like this:
The ASA will still show all of the /32 routes, plus the /25 route:
But routers inside the network will only see the /25 route:
I didn’t talk about modifying any of the OSPF metrics as the routes are being injected, but that would be something to consider if you do this in your environment.
